Reverse Engineering Abandonware - Sierra Studios’ Pharaoh
Introduction:
I was recently hit with a wave of nostalgia thinking about the computer games I used to play as a kid. It occurred to me that my brother, who thankfully holds onto just about everything, had stored a bunch of our old PC games in his room. Sure enough, hidden among them was a personal favorite: Pharaoh, the city building classic by Sierra Studios. Naturally, I decided to see if I could get it running on my current PC and along the way, I wondered if there might be a simple CD check or DRM mechanism I could bypass, and not so much to my surprise there was!
The information provided in this post is for educational and research purposes only, specifically focusing on reverse engineering abandonware and software structures. No malicious intent is implied or encouraged. All examples and technical details are shared under the principles of fair use, to foster learning, inform the community, and the preservation old nostalgic game titles.
Please be aware that reverse engineering and modifying any game or software may violate the terms of service, end-user license agreements, or other legal agreements. if you choose to explore or replicate any of these topics, you do so at your own risk, you assume full responsibility for any consequences, including the risk of voiding warranties, legal repercussions, or other penalties.
Setting the Stage:
First, I used ImgBurn to rip the game to an ISO file and installed it on my computer.
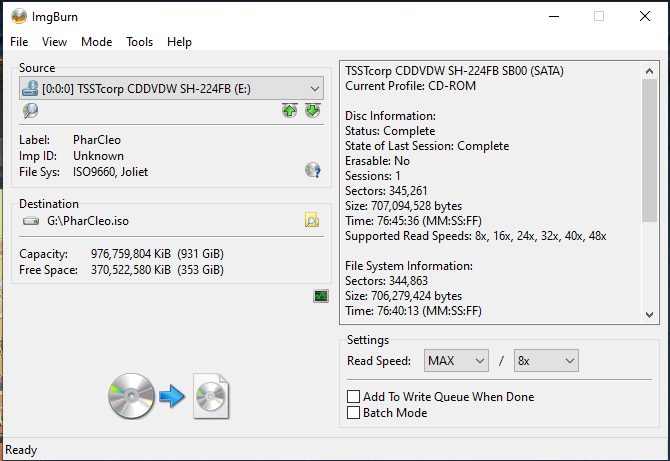
The installation process was just as nostalgic as I remembered complete with that old school installer interface.

Once it finished and I tried to launch the game (without the disc in the drive), I was immediately greeted by the “Please insert the CD” message.
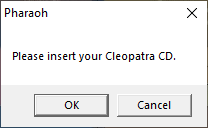
so this turned out to be a straightforward CD check rather than a robust DRM scheme.
Opening Pharaoh in IDA
To confirm how the CD check was implemented, I opened the Pharaoh executable in IDA. Examining the entry point made it quite clear there wasn’t any complex DRM in place just a simple check to see if the disc was present.
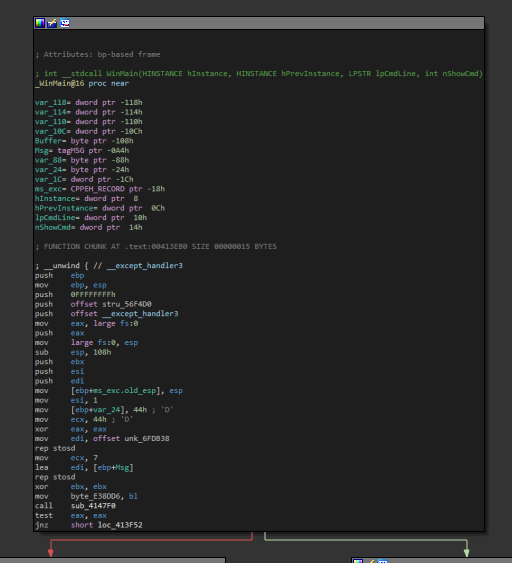
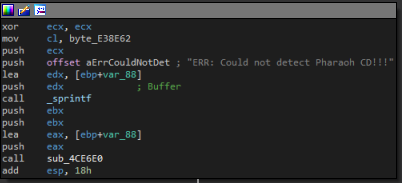
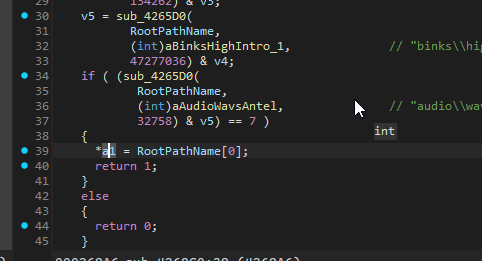
If we quickly look at the function resposible for the CD Check logic we see that upon successful completion, the function stores 1 in eax, uses the first parameter as the drive letter, and returns true.
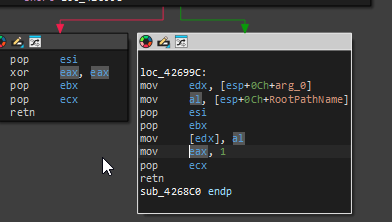
Then then it moves eax into edi and compares the expected value of ebx with edi
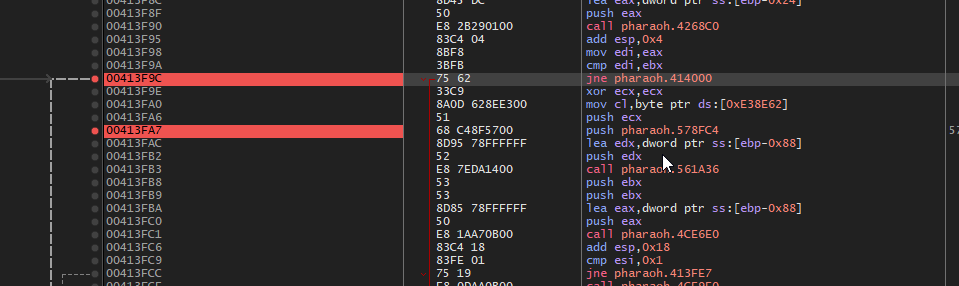
Finally, it jumps to the address pharaoh.414000 if the values are not equal
Relevant Instructions:
; Pseudocode / assembly snippet
; ...
cmp edi, ebx
jne short pharaoh.414000
; ...Changing this instruction from jne to a simple jmp effectively bypasses the check. By doing so, the game no longer cares whether the CD is in your drive.
jmp pharaoh.414000Confirming the Patch
Once I replaced that single instruction, I confirmed that Pharaoh launched just fine without the disc. To be more specific:
- The function you see in IDA appears to load the drive letter into eax, returning a value if it verifies the disc is present.
- That return value gets compared with another register (ebx).
- If they don’t match, the game asks for the CD.
- By changing the jne instruction to a jmp, the game skips the CD check (regardless of the check’s result).
This small patch was all it took to get the game running without the CD.

Wrapping Up
All in all, this was a quick and straightforward little project, perfectly illustrating how simple it can be to patch older abandonware titles. In future posts, I might explore writing a custom mod menu or even injecting some fun cheats into Pharaoh. I’m also planning to tackle a more complicated patching scenario soon, where I’ve run into new (and more challenging) protection mechanisms.
Thanks for reading! If you’re feeling nostalgic for your own favorite classics, there’s never been a better time to dust off those old discs and see what you can get working again.